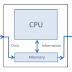
.jpg) the simplified diagram of a microprocessor is shown in fig.5.3. the microprocessor is the portion enclosed by heavy black lines and it is shown connected to the memory unit. we will assume that he program and data is already in memory. there are buses external to the microprocessor and two buses within the microprocessor.the external address and data buses are extension of the some buses inside the microprocessor, so their are really only three different buses, address, data and control. the numbers in bracket in fig.5.3 indicate how many signal lines make up each bus.
the simplified diagram of a microprocessor is shown in fig.5.3. the microprocessor is the portion enclosed by heavy black lines and it is shown connected to the memory unit. we will assume that he program and data is already in memory. there are buses external to the microprocessor and two buses within the microprocessor.the external address and data buses are extension of the some buses inside the microprocessor, so their are really only three different buses, address, data and control. the numbers in bracket in fig.5.3 indicate how many signal lines make up each bus..jpg) the address bus is a 16-bit bus. it carries the 16-bit address code from the microprocessor to the memory unit to the select the memory location which the microprocessor is accessing for a read or write operation. the address bus is unidirectional bus because information flows in only one direction.
the address bus is a 16-bit bus. it carries the 16-bit address code from the microprocessor to the memory unit to the select the memory location which the microprocessor is accessing for a read or write operation. the address bus is unidirectional bus because information flows in only one direction.the data bus is an eight-line bidirectional bus over which 8-bit words can be set from the microprocessor to memory (write operation) or from the memory to the microprocessor (read operation). although, it is called data bus, they information carried on this will not always be data, if will often be instruction codes fetched by the microprocessor.
the control bus is a grouping of all the timing and control signals needed to synchronize the operation of the microprocessor with the other units of the microcomputer. some of the control lines or outputs from the microprocessor from I/O devices. most 8-bit microprocessor have an 8-bit data bus and 16-bit address bus.
 01:31
01:31
.jpg)


.jpg)


.jpg)




.jpg)

.jpg)


.jpg)
.jpg)

.jpg)
.jpg)
.jpg)
.jpg)

.jpg)
.jpg)
.jpg)

.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)





.jpg)
.jpg)
.jpg)